Found myself in a situation I needed to search 20+ documents for a keyword and unfortunately Word cannot search files within a directory for keywords, only the current document. Thankfully we can automate this with PowerShell. The script below will: Accept a directory path and keyword Open each file found and search for the keyword […]
Escalating Privileges to Domain Admin
This method may benefit from some social engineering but will require local Administrator on an machine within the network. Social engineering can be used to speedup the process of enticing a Domain Admin (DA) to login to a system and in-return provide us DA rights. Should you need to obtain local Administrator privileges and you […]
Gaining entry into Windows as Administrator
This is an old but still relevant method of gaining access to an local Administrator account on any windows machine running Vista on-wards. Note: This method will only work when Bitlocker is not enabled on the machine. You can either use a live CD or Windows PE (From Windows installation media), this guide will use […]
Setting up Sysinternals
Whilst Sysinternals can be downloaded and ran from the location to which they are extracted to, there is more preferable way to install on a system in which they will be used more frequently. Download Sysinternals from: https://docs.microsoft.com/en-us/sysinternals/ Extract the downloaded zip contents to: C:\Program Files (x86)\SYSINT Extracting to this directory is useful for white-listing Run […]
IIS Server Header Hardening
You may want to remove the server version from your HTTP response for security reasons, there are a couple ways you can go about this depending on how the header is being handled. Microsoft-HTTPAPI/2.0 If you are seeing the Server header Microsoft-HTTPAPI/2.0 then the header is being managed by HTTP.SYS driver and is not being […]
Running TOR on Kali | The proper way
TOR shouldn’t be run as root. Many guides gloss over this by removing the root check in the start-tor-browser.desktop file, here is the better way: Create a new user: adduser –home-dir /home/kali kali Download and extract TOR from https://www.torproject.org/projects/torbrowser.html.en Add the newly created user to the xhost file: xhost si:localuser:kali Copy the extracted TOR files to the […]
Setting up OpenVPN on Kali
Here is how to set-up OpenVPN on Kali. The process is (unsurprisingly the same for Debian), steps below: Obtain OpenVPN certificates, key and openvpn.ovpn files from the provider ca.crt: This is the certificate of the certification authority client.crt: This is the user certification file client.key: This is your private key file openvpn.ovpn: This is your OpenVPN configuration file Rename the openvpn.ovpn config […]
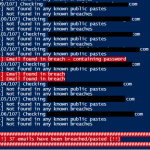
Finding pwned emails with HIBP and Powershell
This small project uses Troy Hunts’ Have I Been Pwned fantastic (API) service along side a PS module which parses the JSON from the API. The purpose of this script is to read in emails addresses from file and then check them against HIBP to see if they are apart of any breaches or public […]
Minecraft Random MOTD Selector
A fun micro-project, this Powershell script will select a random message of the day (MOTD) and write it to disk.
Finding users in AD and adding to distribution group
I had a scenario in which a group of users needed to be added to a distribution group hosted on Exchange online. So I thought Id made a little script which pulls users from the local Active Directory; checks them against the distribution group and if they are not present, adds them. You may want […]